DUO
Multi-Factor Authentication (MFA) from Duo
Securing the Workforce with Duo
Duo Multi-factor Authentication is the best product to protect your business because it provides multiple ways to validate login credentials while keeping phishers and hackers away from your data.
Securing the Workforce with Duo
Eighty percent of security breaches involve compromised passwords. Duo can help cut down on these problems because even with your password they will be blocked from accessing the system by multi-factor authentication.
In addition Duo allows you to go mobile and verify your logins right from your phone so you don't have to worry about trading efficiency for security like with other two factor authentication methods.
For organizations of all sizes that need to protect sensitive data at scale, Duo’s trusted access solution is a user-centric zero-trust security platform for all users, all devices and all applications. Duo is considered to be the most simple and quick 2FA/MFA on the market.
It seems that they designed this product with every possibility covered. They will let you securely access your applications regardless of the current situation. Many other authentication services leave users out to dry when they fail to follow protocol. However, Duo seems designed with these situations in mind. You can authenticate without your phone, without a passcode, and even without an internet connection. Using a variety of ways to verify identity Duo lets you choose the perfect way to manage your authentication. It doesn't end there though, Duo includes devices that have biometric scanners. Duo allows you to authenticate from your fingerprint or using other biometric devices that securely verify your identity instantly.
Security Breaches
Modern, Effective Multi-Factor Authentication
Multi-factor authentication from Duo protects your applications by using a second source of validation, like a phone or token, to verify user identity before granting access. Duo is engineered to provide a simple, streamlined login experience for every user and application, and as a cloud-based solution, it integrates easily with your existing technology.
YOU SHOULD KNOW
80% of security breaches involve compromised passwords.
2019 Data Breach Investigations Report, Verizon - via DBIR Interactive
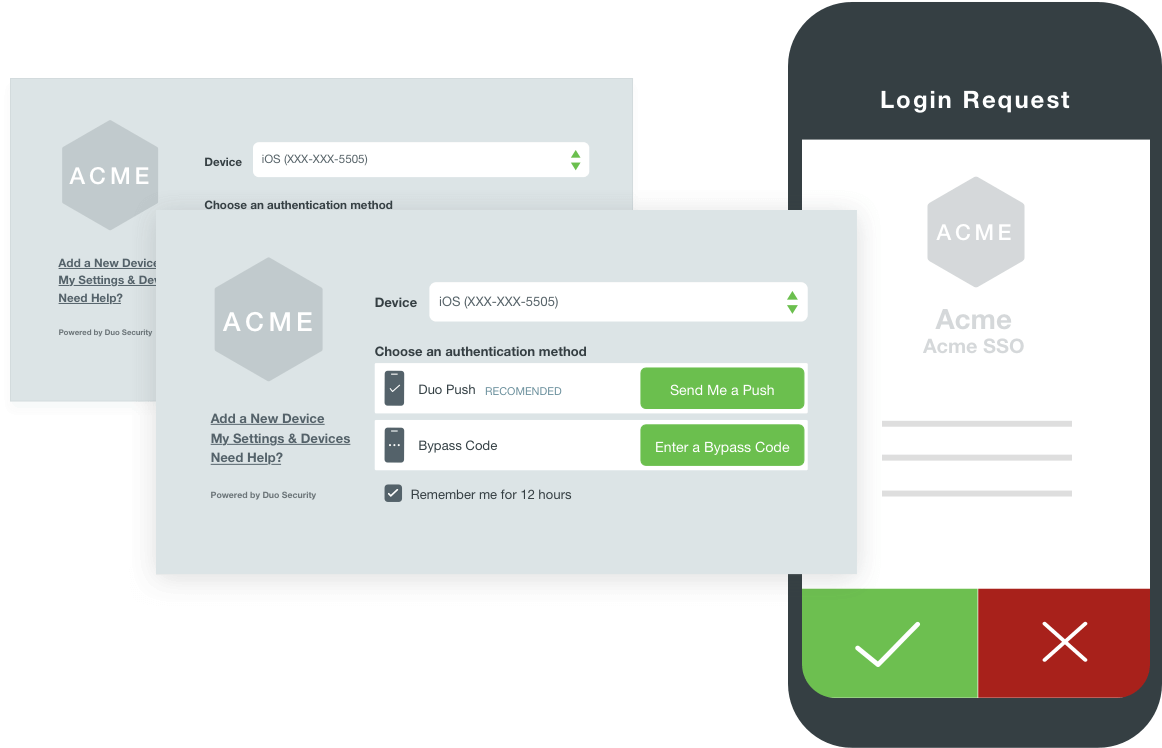
Duo runs from the cloud so it can scale with your business as you grow or as your needs change. It has a simple interface and can work with legacy technologies as well, making setup much easier than other authentication solutions. When setting up your business you can also choose to have users self enroll and select their own verification methods so that you have the ideal security solution for each of your employees. The flexibility of these authentication services is what makes them so powerful, you can use Duo for remote access, controlling critical infrastructure, securing custom applications, or even offline devices. Duo even provides support for Multi-cloud, hybrid, or on-premises environments. The reporting features Duo offers are very detailed and give you a simple way to manage and view how authentication is running within your company. Using frictionless authentication management you can keep an eye on your business's safety right from your browser.
Ease of Use
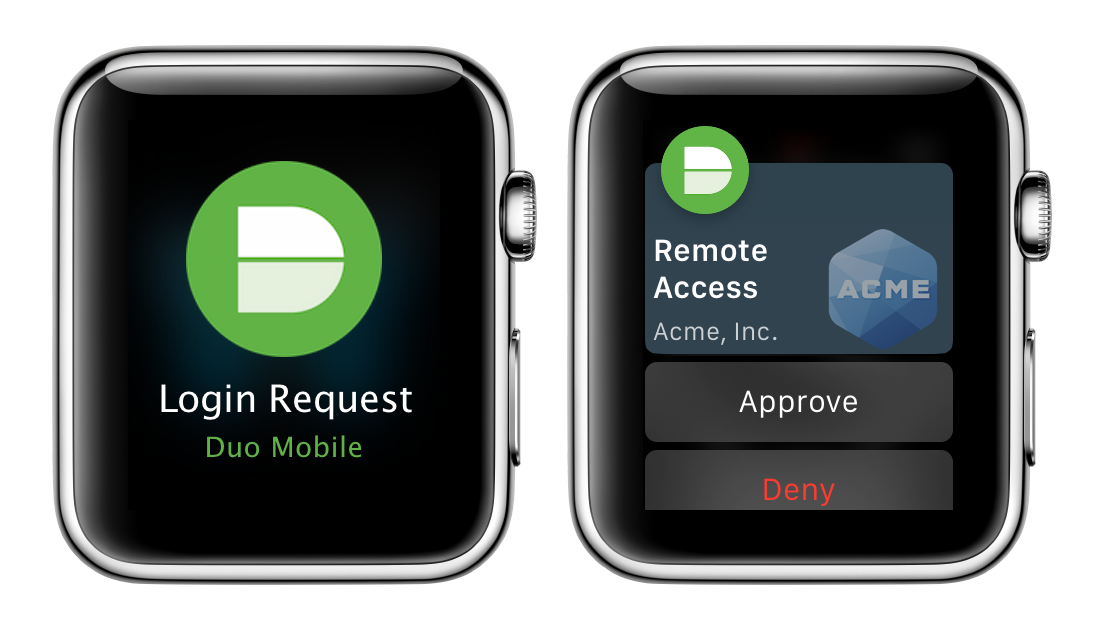
If you need more traditional authentication then don't worry, Duo also has support for older methods of verification such as using tokens or passwords to verify identity. There are also solutions in between such as verifying your identity with one tap from your mobile device using the Duo Mobile app with the Duo Push feature. There are solutions for every user so if you need to increase your company's security without a hassle Elevate Technology recommends using Duo Security from Cisco.
Duo Pricing
-
$3
Duo MFA
-
$6
Duo Access
-
$9
Duo Beyond
-
$3
Duo MFA
-
$6
Duo Access
-
$9
Duo Beyond
Don’t know what to choose?
This email address is being protected from spambots. You need JavaScript enabled to view it. us to get help with your plan.
- Hits: 3903